导读
2017年以来,区块链项目出现了井喷式地上升,然而在喜人增长态势的背后,人们也注意到大部分项目都缺乏与其它区块链项目互连互通的能力而成为孤立的网络体系。
因此,跨链技术也逐渐进入了大家的视野,本文将为大家解读一个跨链项目Cosmos,看看它是如何做到让不同区块链的价值网络实现互通的。通过对该项目的解读,让大家对跨链项目有个初步的了解。
同时受限于篇幅,我们会分为上下两篇,上篇让大家了解了Cosmos的核心技术Tendermint,详情可见上篇:深度剖析区块链跨链技术Cosmos(上篇)。此篇将为大家着重介绍Cosmos。
跨链技术背景
随着区块链技术的火热,越来越多的企业和开发人员加入到区块链的浪潮中,市面上也出现了许多不同类型的链,应用在金融、健康医疗、供应链、资产管理和溯源等领域。然而大部分链上应用(加密货币或者智能合约)都无法跨越当前链的边界,不能与其他链协同合作实现价值的流通从而限制了区块链的发挥空间。如何能让不同类型的链协同合作实现价值的流通成了探索的方向,这也是跨链技术的起因。跨链技术是打开链与链之间互通的钥匙,能很好地解决价值孤岛的问题,建立价值网络的桥梁。
目前主流的跨链技术包括:
- 公证人机制(Notary schemes)
- 侧链/中继(Side chains/relays)
- 哈希锁定(Hash-locking)
- 分布式私钥控制(Distributed private key control)
而本文所要介绍的主角Cosmos就是中继技术的一个典型案例,接下来将逐步为大家揭开Cosmos的面纱。
Cosmos概述
Cosmos是Tendermint团队推出的一个支持跨链交互的异构网络,它最终的目标是创建一个区块链互联网,允许大量自主且易开发的区块链互相扩展和交互。基于Tendermint开发,采用的Tendermint共识算法,是一个类似实用拜占庭容错共识引擎,具有高性能、一致性、具备拜占庭容错等特点。关于Tendermint的详细介绍可以参考本文上篇:深度剖析区块链跨链技术Cosmos(上篇)。
Cosmos网络由许多独立的并行区块链组成,网络中第一个区块链是Cosmos Hub,其他的并行链称为Zone,通过跨链协议(IBC)与Hub进行跨链操作。
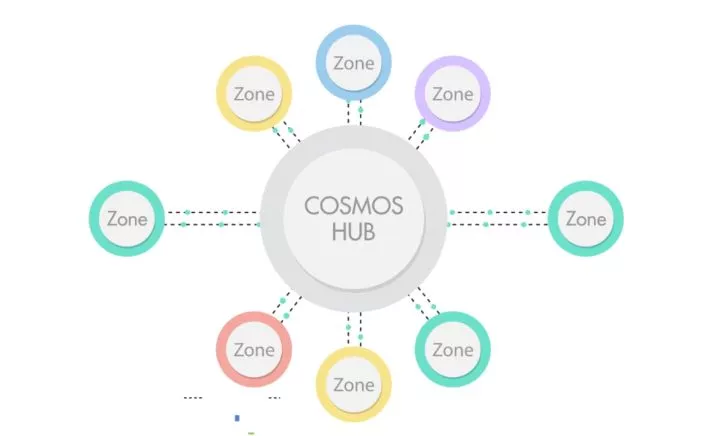
目前Cosmos Hub已经经过了多个版本的迭代,MVP版本也趋于完成,同时测试网络也在前不久更新到gaia-7001,但主网的上线时间团队还未给出,所以对Cosmos感兴趣的朋友还需要一些耐心。
Cosmos架构
从Github上可以看出Cosmos主要的代码是cosmos-sdk,它包含Cosmos Hub的程序代码,同时也是一个区块链开发框架,为其他区块链开发者提供一些通用的功能模块,比如:共识,P2P网络,IBC,账户,治理,认证等。大致框架如下:
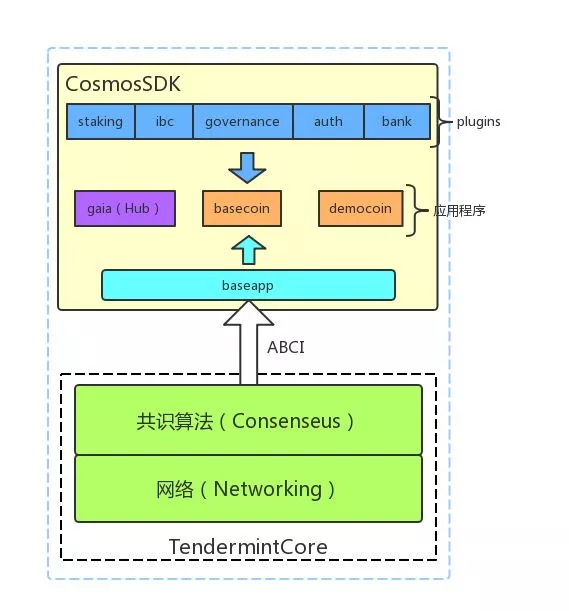
不难看出cosmos-sdk其实就是一个ABCI应用。主要有:
- baseapp:定义了一个基本ABCI应用的模版,与Tendermint通信。开发者也可以根据自己的需求重写。
- 应用程序:包括gaia、basecoin、democoin。其中gaia就是hub主程序,basecoin以及democoin是提供的两个示例应用。
- plugins:cosmos-sdk的基本单元,每个plugin都是baseapp的功能扩展,包含各自的消息和交易处理逻辑。目前SDK已经集成了一些重要的
- staking:POS相关的实现,包括:绑定,解绑,通货膨胀,费用等操作。
- ibc:跨链协议IBC的实现,也是Cosmos支持跨链的主要插件。
- governance:治理相关的实现,如提议、投票等。
- auth:定义了一个标准的多资产账户结构(BaseAccount),开发者可以直接嵌入自己的账户体系中。
- bank:定义资产的转移。
因此基于cosmos-sdk框架,利用其插件功能,可以非常快速的开发出属于自己应用的区块链,同时也可以很方便的加入Cosmos生态网络,支持不同链之间的互操作,在插件的设计上和EOS也有异曲同工之妙。
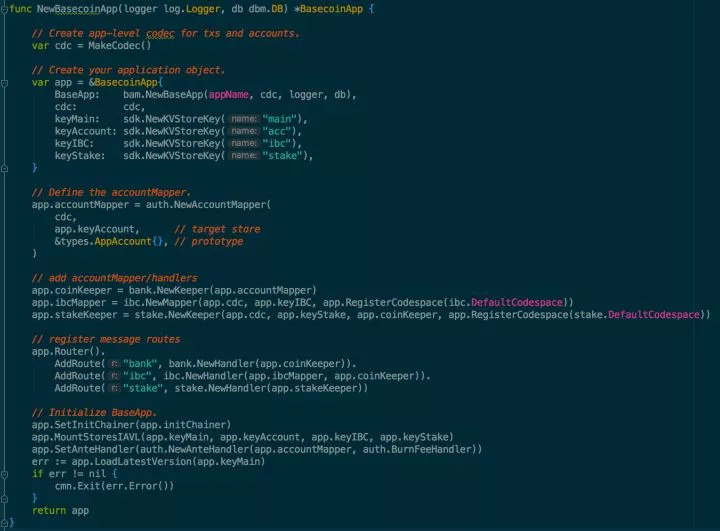
那么如何使用这些插件功能呢?可以参考cosmos-sdk提供的示例应用,以basecoin为例,只需要几步:
- 创建自己的ABCI应用,可以嵌入baseapp,也可以重载baseapp。
- 定义自己的账户体系,可以嵌入BaseAccount。
- 选择所需要的插件,注册到消息路由。
Cosmos跨链
Tendermint团队在15年就开始考虑跨链技术,跨链也是Cosmos网络最重要的一个特性。一般来说,实现跨链需要做到:
- 共识算法需要具备及时最终性,也就是说在出块之后,需要能够快速确认为不可逆(固定不变)。
- 交易确认需要高效独立的证明方法,目前的做法都是基于Merkle证明。
基于cosmos-sdk的区块链使用了Tendermint共识算法就非常容易能够做到。除此之外,Cosmos的区块链间通信协议(IBC)将不同区块链连接起来,达到价值转移的目的。
IBC协议
IBC协议是针对Cosmos网络设计的,依赖其及时最终性的特点,用于Hub与Zone之间消息传递。IBC协议中设计了两个消息:
- IBCBlockCommitTx:发送方所在区块链的最新的区块信息。
- IBCPacketTx:跨链交易本身的信息,及其在发送方链中被打包的区块信息。
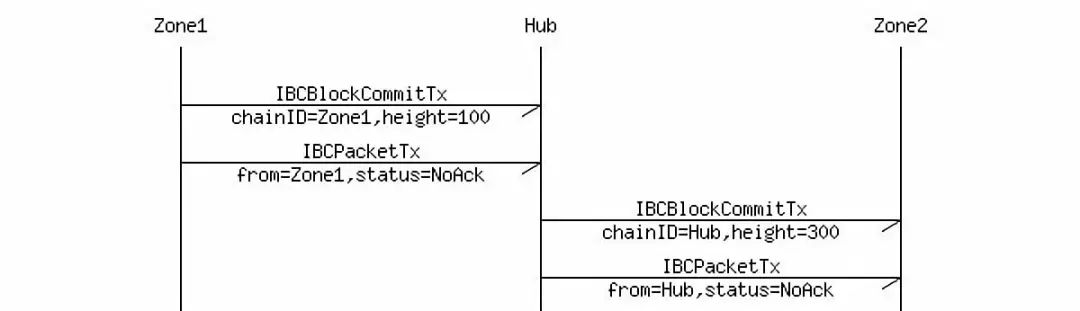
但有了消息的传递,接收链如何校验信任消息呢?
在IBC协议设计里,两个链建立连接之前需要进行彼此注册,有两个作用:
- 保存对方链验证者集合以及Merkle证明的算法,这样接收链才能确保消息的正确性和来源的可靠性。
- 为对方链创建两个可靠队列,一个队列存放所有发送对方链的消息(outgoing),一个队列存放来自对方链的消息(incoming)。
我们以chain1中用户User A转100mycoin 给test-hub用户User B为例看看IBC整个的工作流程如下(基于目前IBC实现代码):
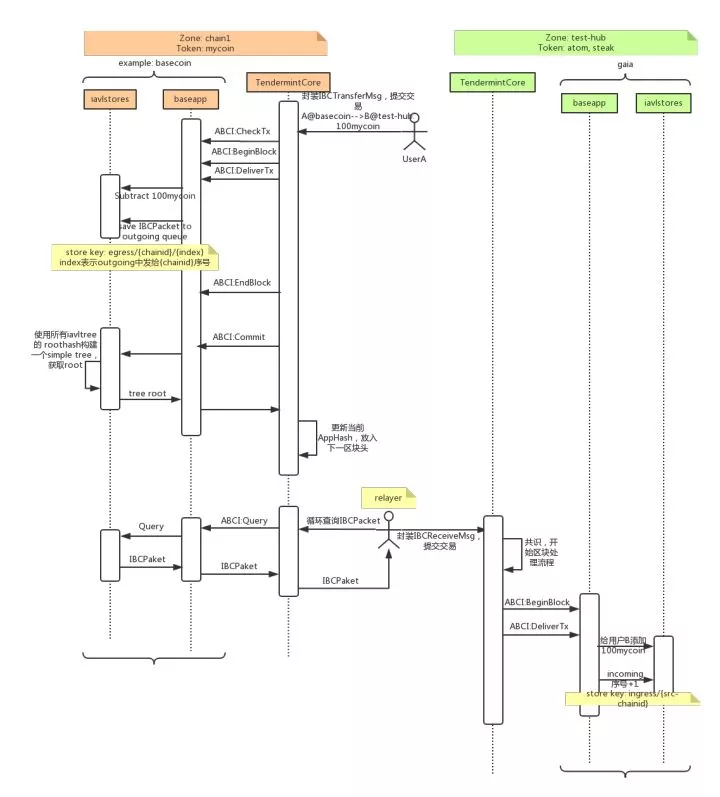
整个工作流程可以分为三个阶段:
- User A向chain1提交跨链交易,chain1执行该交易,并将交易存入outgoing队列。
- relayer从chain1中对应test-hub的outgoing消息队列取出跨链交易,提交到test-hub。
- test-hub执行交易,放入incoming消息队列。
大家可以看到,整个流程比较简单,而且涉及的消息只有IBCPacket。目前Cosmos跨链实现并没有全部完成,只是完成了一个简单的交易处理流程。
PegZone
基于cosmos-sdk开发的区块链能够轻松满足实时最终性,然而现存的Bitcoin和Ethereum这类使用POW共识的区块链并不具备此特点,只能属于概率最终性,无法防止区块链的回滚。对于这类链,团队采用PegZone方案来解决。
PegZone本身其实是一条代理链,实时跟踪原始链的状态,通过设定一个安全阀值,等待原始链区块增长数达到安全阀值时就认为原始链的状态达到了伪实时最终性(回滚概率小),这点和轻客户端钱包验证是相同的原理,例如比特币安全阀值通常设置为6,以太坊安全阀值可以设置为20或者100。而PegZone本身具备实时最终性,就可以通过IBC与Hub相连,从而实现跨链。
接下来还是用例子来说明下,以Ethereum为例来看,有兴趣的朋友可参考Github上的cosmos/Peggy项目。示意图如下:
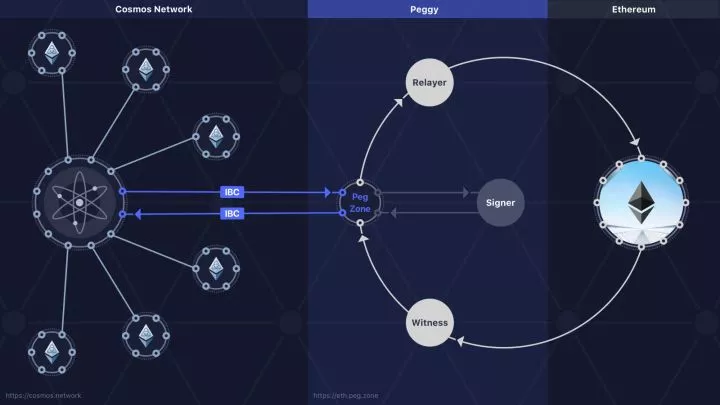
上图我们可以看出PegZone可以分为5个部分:
- Smart Contract:资产托管的角色,保管以太坊中的代币和Cosmos中的代币。主要提供了lock、unlock、mint、burn四个方法。
- Witness:是一个以太坊全节点,监听以太坊合约的event,并等待100个区块产生后,封装WitnessTx提交到PegZone中来证明在以太坊内状态更改。
- PegZone:PegZone是基于Tendermint的区块链,负责维护用户的账户信息,允许用户之间资产的转移,并提供交易查询。
- Signer:使用secp256k1对交易进行签名,以便签名能够高效的被智能合约验证,对应于智能合约的校验者公钥集合。
- Relayer: 中继器负责交易转发。将所有Signer签名后的SignTx转发到smart contract中。
现状
跨链是Cosmos的重要特性,但在从目前的代码实现上感觉有些遗憾:
- IBC协议目前只完成了基本消息的传递功能,并没有安全校验、注册机制以及一些异常的处理。
- PegZone机制处于暂停状态,机制设计上团队也称处于实验性质。
- 对于没有基于cosmos-sdk开发,但符合实时最终性的链无法使用IBC,无法做到异构链的兼容。它们可能使用不同的:
- 签名算法
- 序列化方法
- Merkle证明的方式
总结
通过上下两篇文章,从架构,核心技术——Tendermint、跨链、源码以及现状等方面对Cosmos进行了详细介绍。整体来讲,Cosmos更偏向于一个区块链开发框架,让开发者可以只需要专注于自身业务而不需要考虑区块链底层技术实现,所以在架构设计上采用了灵巧的插件设计,开发者可以按需使用。
Cosmos跨链协议部分从代码上看,完成度还不太高,有些遗憾。并且设计上跨链交易都需要通过Cosmos Hub,这样会过于依赖Hub,对Hub本身的承载压力是个考验,目前其他的一些跨链实现方案也都需要依赖自身的一条链,都会存在这个问题。笔者觉得跨链未来会发展成标准化协议,就像TCP之于互联网,而不是依赖某条具体链,通过定义标准化的模块,通过路由将跨链交易转到目标链,目标链完成对原始链的校验后,确认交易合法性,并执行交易。设想示意图如下:
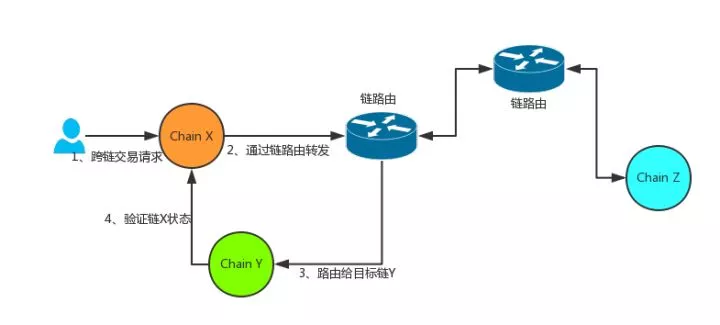
转载自:https://mp.weixin.qq.com/s?__biz=MzUyMjg0MzIxMA==&mid=2247483744&idx=1&sn=02baaff744429c37626dc89aed14988f&chksm=f9c4e445ceb36d53578bd8c22af2ea14023be0b787a4d980702ed0246a02a1229296e0fe53c1&scene=0






