https://swarm.ethereum.org/
https://docs.ethswarm.org/docs/
https://github.com/ethersphere
https://swarm-guide.readthedocs.io/en/latest/introduction.html
https://mp.weixin.qq.com/s/splSwJ3cf2-uEbc2LC5M_w
https://mp.weixin.qq.com/s/FP3UJwwfRLt1gauEZcOKHw
Chia 分布式部署详细文档
最近社区很多小伙伴来询问Chia分布式部署的方法,那我们今天就写一下Chia分布式的步骤以及测试环境验证
分布式的逻辑
其实前面已经写过部署的草稿了《Chia 分布式部署文档》,但是由于当时时间紧,对于没有开发基础的小伙伴理解上还是有些难度。
下面我们详细说下分布式拆分原理以及注意事项
下面是Chia架构模块结构
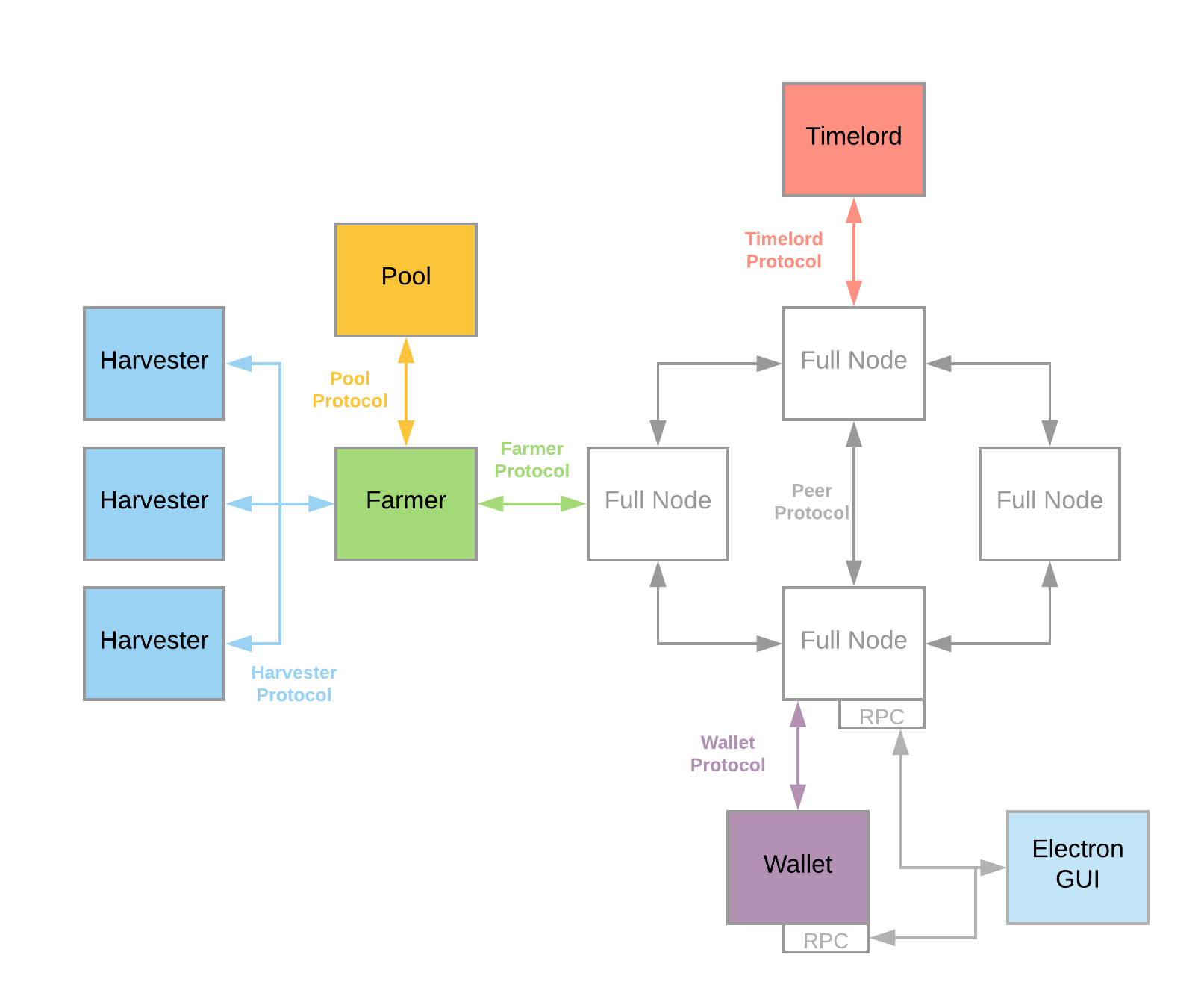
简单说每个模块都是单独的程序,都是通过TCP连接的,对于Chia Gui程序,默认运行是把各个模块都运行在本地,localhost连接的。对于分布式来说,就是把各个模块根据功能和负载等因素分不到不同机器。
模拟生产环境
由于plots存储量体量无上限,并且数据可重新生成,对于存储量和数据安全来说,优先选择存储量,所以单盘存储,不做raid。
对于专门做Chia挖矿的,一般的硬件配置是搞一部分配置稍微好的机器做P盘机(绘图机/work机..){稍后会专门写一篇推荐生产P盘配置的文章},一些二手的存储机做存储(服务器前部分是磁盘阵列),P盘机硬件配置存储部分只有SSD临时绘图用,最终的plots存储到存储机《为Chia P盘机器提供存储服务》
此篇文章我们主要讲挖矿的分布式,对于P盘自动化,后面会有专门的程序和文章做讲解。
生产环境中,一般是把所有的机器放到一个IDC机房,或者自己来管理,所以模块内服务器都是内网连接,网络环境相对简单。
中控高度可控
对于系统化架构的设计大致如下,各模块彼此低耦合,对于一台机器只要装上中控子服务,配置好Chia中控调度地址,Chia中控调度服务会自动配置该机器的环境,并自动下发相应的任务,减少用户的学习成本。
也可以用于推广绘图算力和绘图存储,
用户只需要安装对应中控子服务(绘图/存储),Chia中控调度中心即可自动下发对应的任务,对于绘图任务类似POW,根据用户绘图量用户得到相应的奖励。
用户也可以选择存储任务,此时中控子服务会下发已经会好的图,用户无感知,只需要准备好足够容量的存储空间即可,子服务会自动安装好Harvester相关服务配置,中控调度只需要定时检查用户存储状态和网络环境,就可以根据工作量进行奖励发放。当然发放的可以别的链的对应代币,可以用于对冲推广代币等。
只是对调度服务的另一个使用场景吧,
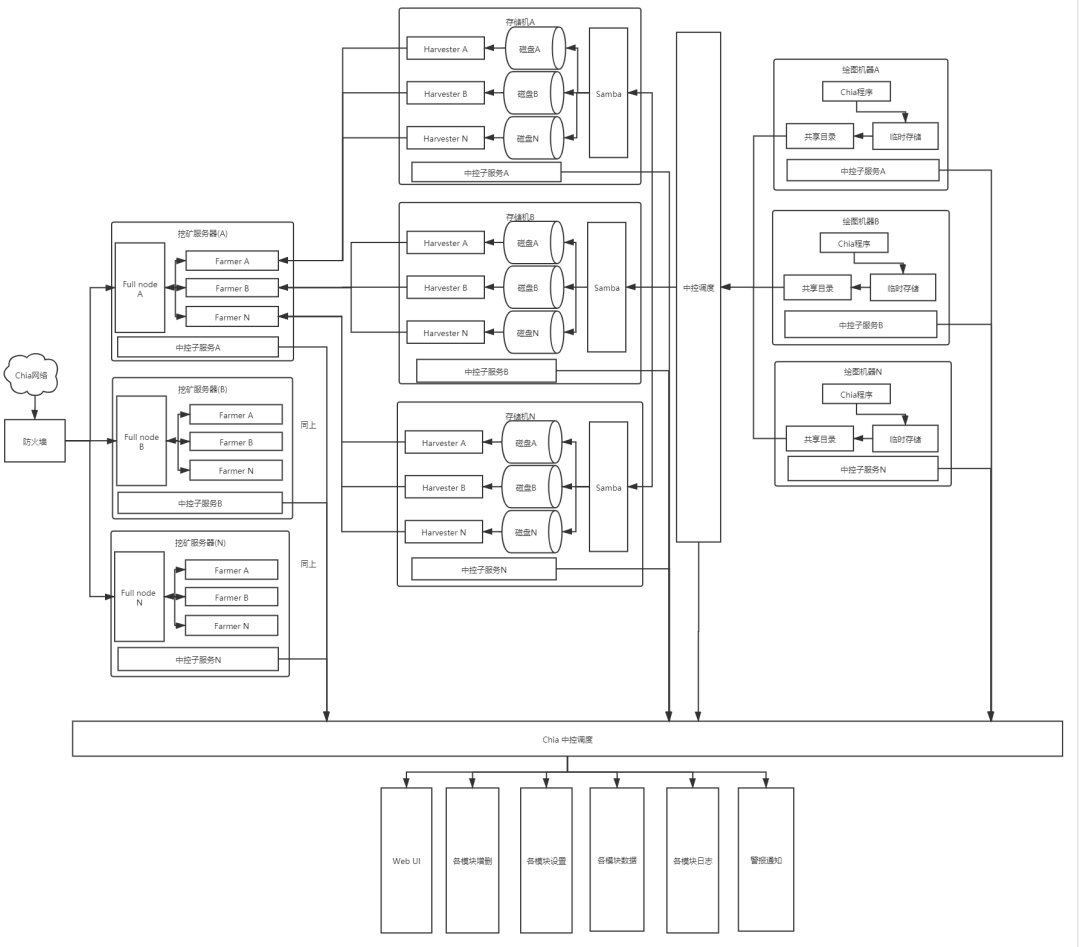
后面社区也许会推出整体服务,暂时不确定
对于没有开发能力的,架构中的中控服务可以先用人工来代替
简化后架构如下
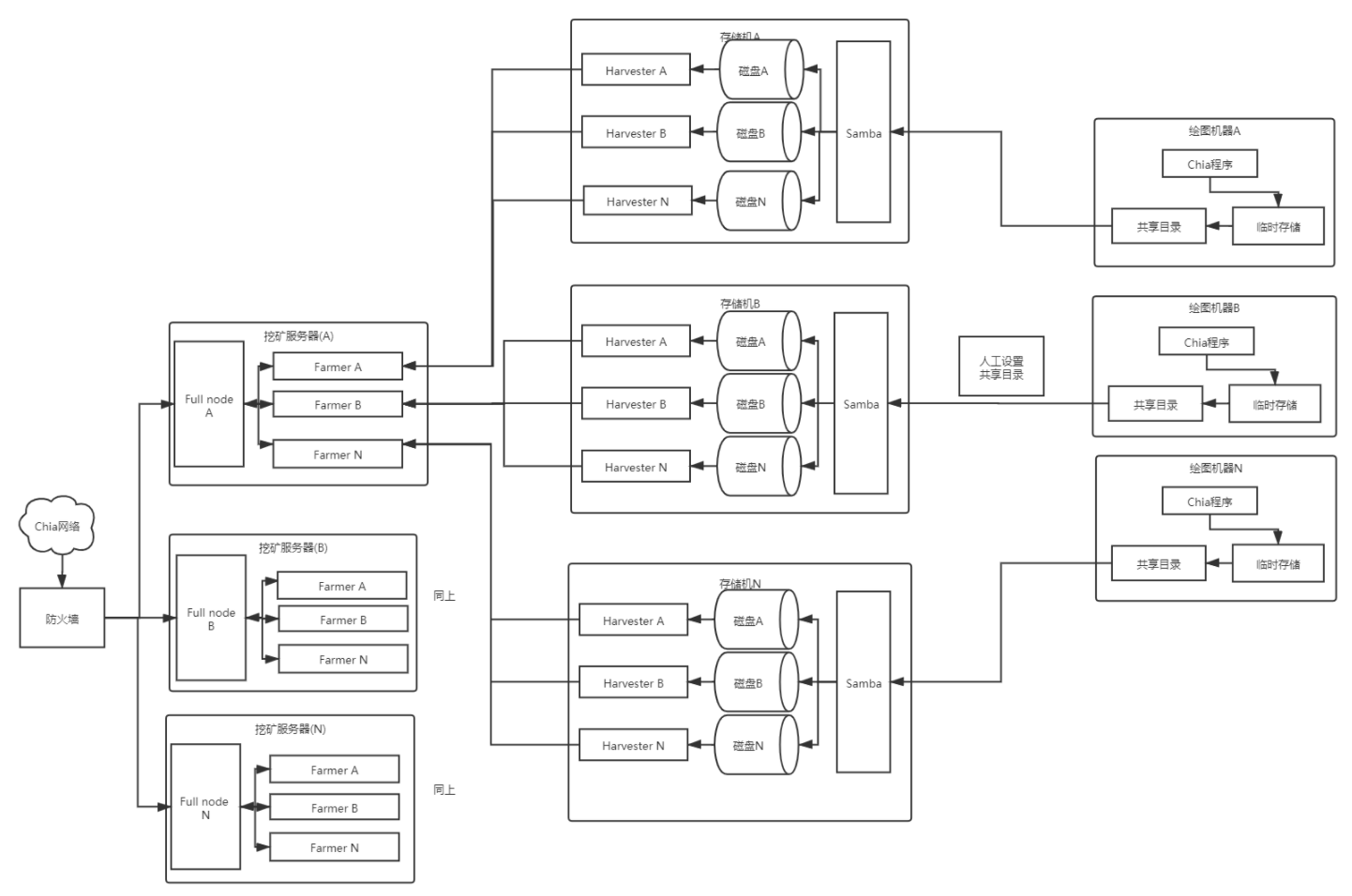
对于各模块的增改也先人工处理
实际测试
我们来演示最基础的分布式挖矿配置,一台挖矿服务器和两台存储服务器之前的配置,以及验证配置是否正确。
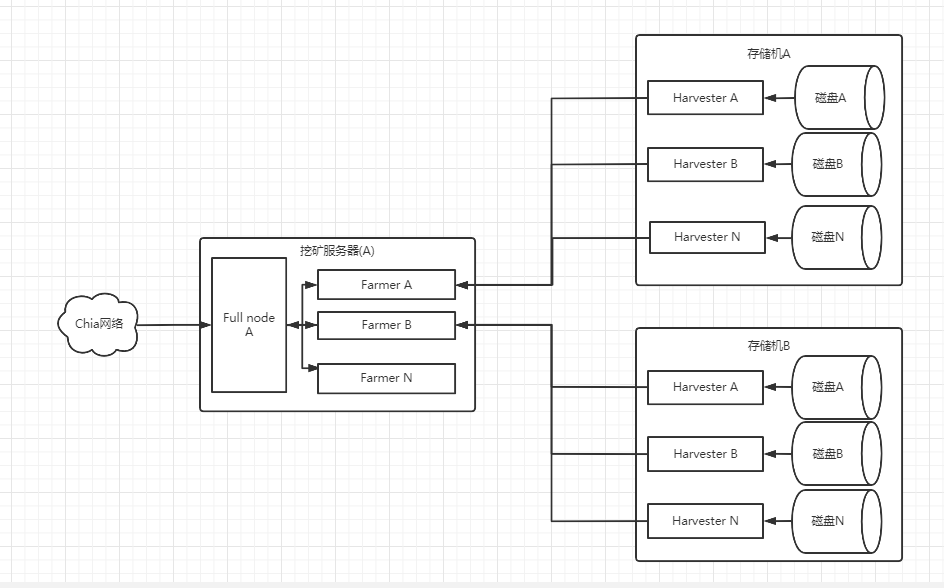
稍后继续补充
Chia 源代码编译安装
操作系统
Ubuntu 20.04
编译
sudo apt-get update
sudo apt-get upgrade -y
# Checkout the source and install
git clone https://github.com/Chia-Network/chia-blockchain.git -b latest
cd chia-blockchain
sh install.sh
. ./activate
# The GUI requires you have Ubuntu Desktop or a similar windowing system installed.
# You can not install and run the GUI as root
sh install-gui.sh
cd chia-blockchain-gui
npm run electron &升级
cd chia-blockchain
chia stop -d all
deactivate
git fetch
git checkout latest
git pull
# If you get RELEASE.dev0 then delete the package-lock.json in chia-blockchain-gui and install.sh again
sh install.sh
. ./activate
chia init
# The GUI requires you have Ubuntu Desktop or a similar windowing system installed.
# You can not install and run the GUI as root
sh install-gui.sh
cd chia-blockchain-gui
npm run electron &参考
https://github.com/Chia-Network/chia-blockchain/wiki/INSTALL#ubuntudebian
使用Chia Gui程序P数据的简单使用
下载 Chia GUI 程序
Windows下载地址: https://github.com/Chia-Network/chia-blockchain/releases/download/1.0.5/ChiaSetup-1.0.5.exe
然后安装完启动
启动程序
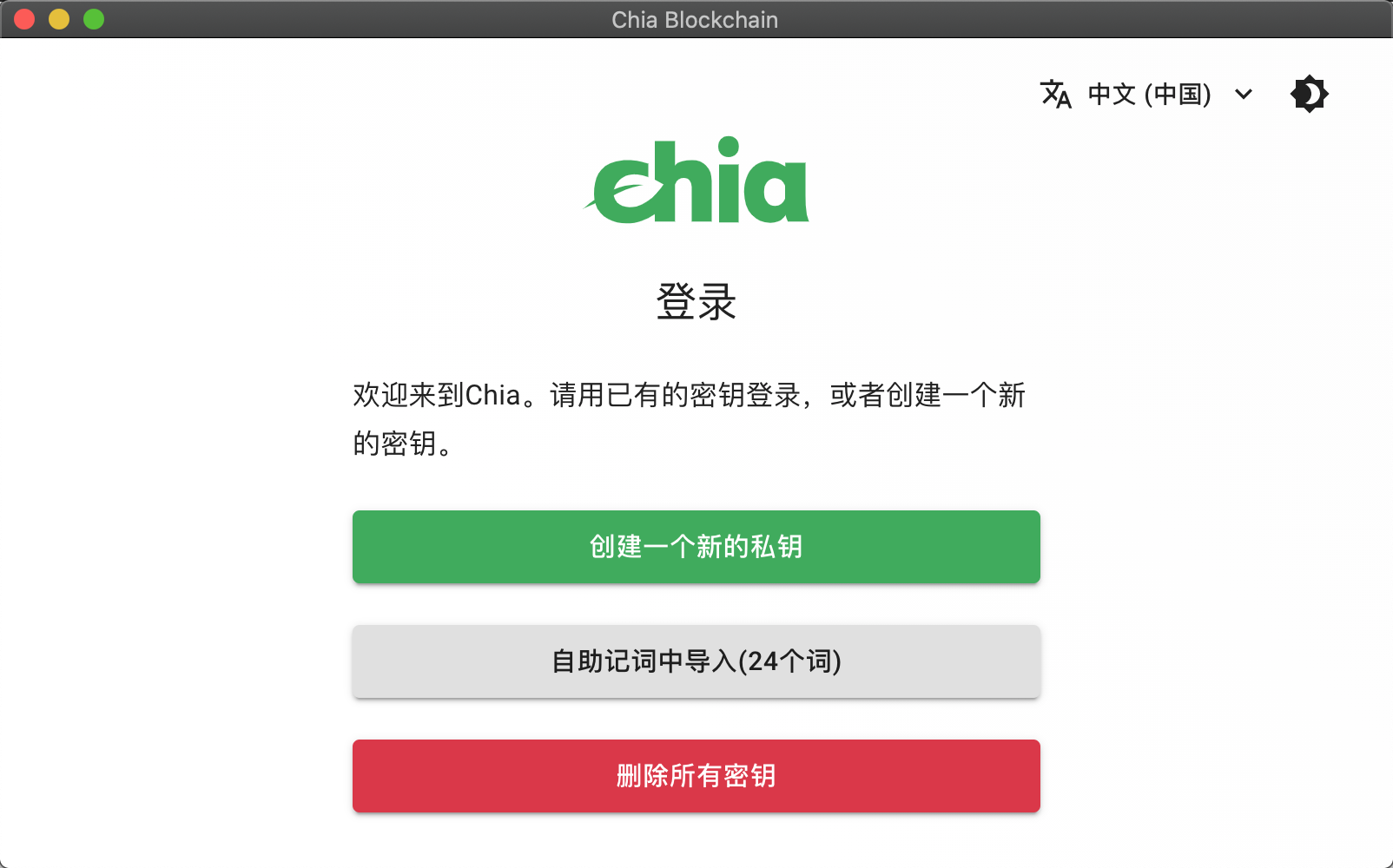
如果之前有创建过账户,则点击“自助记词中导入(24个词)”,如果没有的话,直接点击“创建一个新的私钥”
创建一个新的私钥
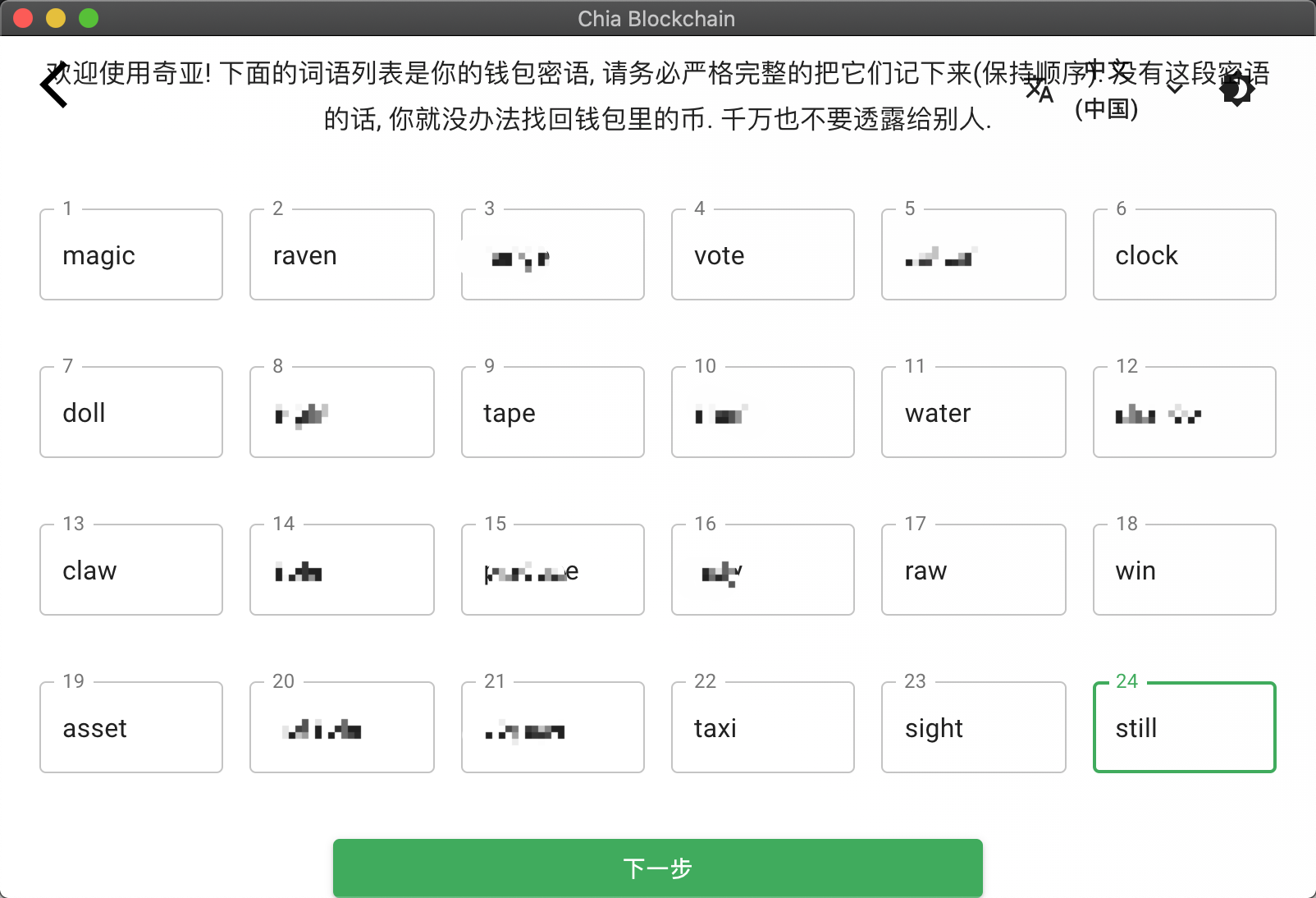
把助记词保存好,最好手抄到文件,存放到安全的地方
点击下一步,进入主程序
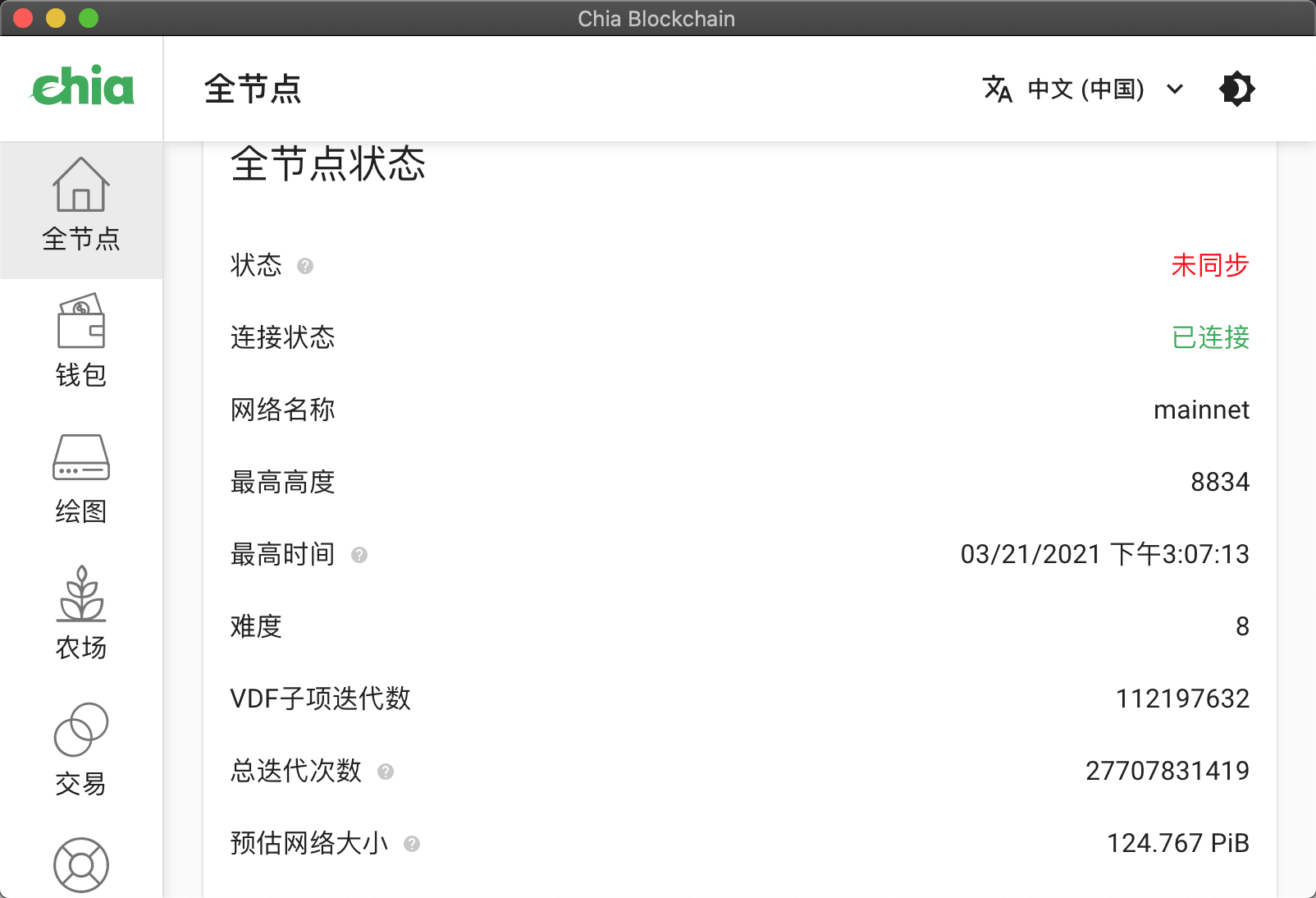
确认“连接状态”为“已连接”,对于“状态”刚开始运行时会显示“未同步”,稍微等等就好了.
开始P数据
点击“绘图”
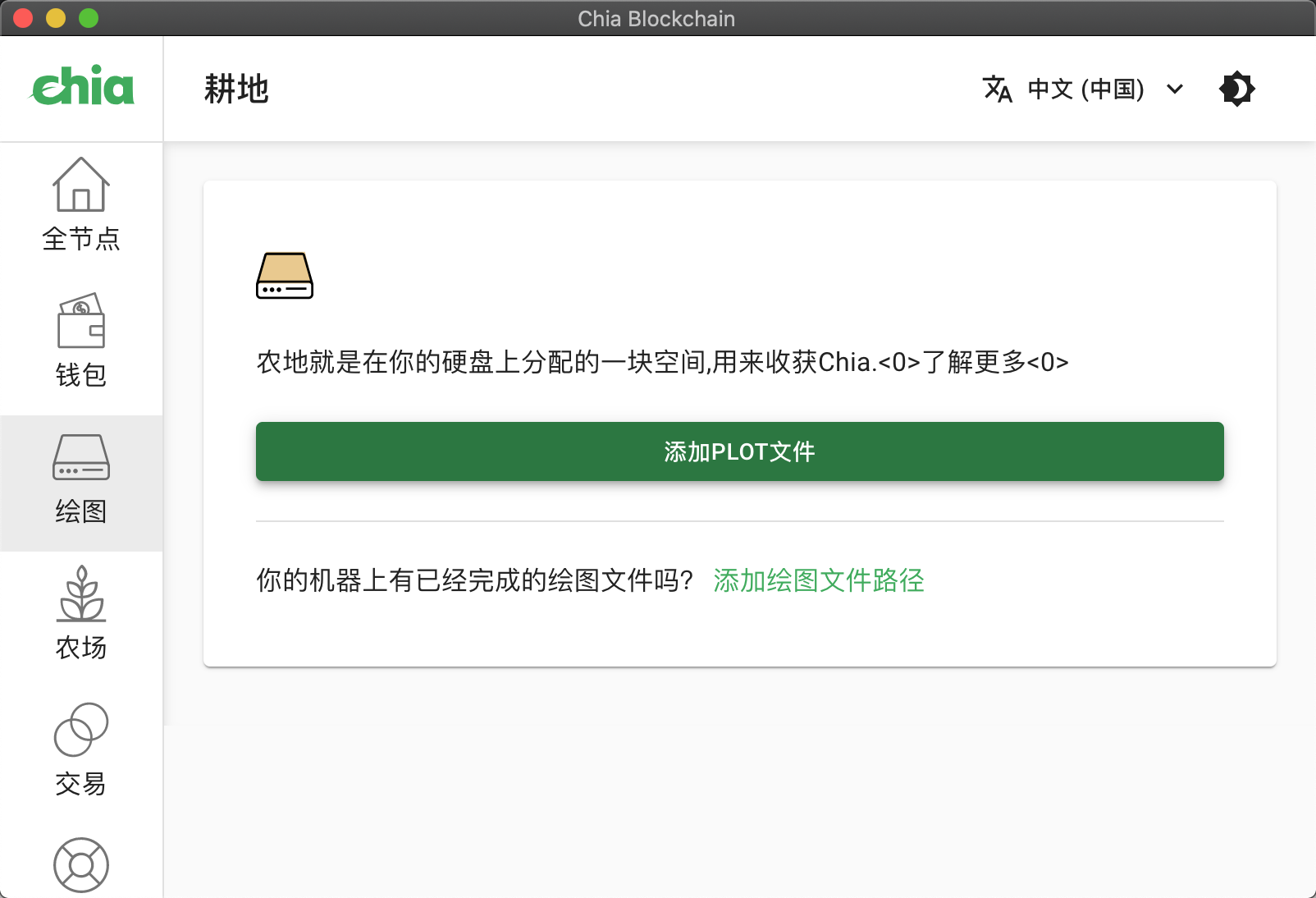
点击“添加PLOT文件”
分别对各个选项做设置
1. 选择Plot文件大小
确认“选择Plot文件大小”选择的是“101.04GiB(k=32 ...)”
目前这个是主网最优的选项, 对于测试网可以选择“600MiB(k=25 ...)”
2. 选择要拓荒的数量
绘图数设置为 当前机器CPU 总核心数相等的数(即为2线程一个任务)
并选择“并发拓荒”
备注
如果想设置单线程跑一个任务,则点击“显示高级选项”,修改线程数量为1, 同时上一步中的绘图数设置为CPU核心数的2倍.
3. 选择临时目录
选择存放临时数据的存储目录
这个是P数据时计算需要的临时空间,这个存储需要较高的读写速度,不然严重影响P盘速度
单个任务大概需要304G空间.
4. 选择最终目录
选择最终P数据的生成位置,也就是单独的存储服务器的存储目录.
存储服务部署,可以查看《为Chia P盘机器提供存储服务》
为Chia P盘机器提供存储服务
逻辑简述
简单来说就是P盘机器专门用来生产plots, 单独的机器用来存储为收割机程序消费.
所以需要搭建存储服务,对于服务选择来说有nfs 和samba等,此片文件将使用samba来部署.
环境搭建
假设P盘机器(A)ip为:192.168.2.152
存储机器(B)ip为:192.168.2.142
B机器
安装samba
sudo apt-get upgrade
sudo dpkg -l | grep samba
sudo apt-get install samba samba-commonB机器生产环境为磁盘阵列,为了避免数据损坏,以及存储最大化,单盘使用. 为每个盘做raid0(因为服务器前部磁盘通常链接的板卡必须要做硬raid,所以即使单硬盘使用,也需要每个磁盘做raid0,不然不识别,设置在bios中)
下面在samba服务配置文件中,为每个磁盘做共享目录设置
设置samba配置
我们拿其中一个硬盘做举例,其余的盘操作相同
sudo vi /etc/samba/smb.conf假设第一个磁盘挂载路径为 /mnt/md0.
把当前存储机登陆账户tom添加到samba服务
sudo pdbedit -a -u tom
sudo pdbedit -L因为主要是内网使用, 直接使用当前系统账户登陆了,也可以单独创建账户登陆,因为文件写入时和当前配置账户是同一个组,避免数据权限问题.
在文件最后添加
[md0]
comment = md0
path = /mnt/md0
public = no
browseable = yes
writable = yes
available = yes
valid users = tom其他的磁盘逻辑同上.
重启 Samba 服务
sudo service smbd restart处理完成后,存储机的配置就完成了,为每个存储磁盘创建了共享.
A机器
安装cifs samba
sudo apt-get install cifs-utils samba手动将md0 挂载到当前机器目录/home/tom/md0
查看B机器uid, 在B机器终端输入id
sudo mount.cifs //192.168.2.142/md0 /home/tom/md0 --verbose -o
username="tom",password="123456",uid=1000,iocharset=utf8,rw,dir_mode=
0777,file_mode=0777此时B机器的md0共享目录就被挂载到/home/tom/md0,并且只需要当前登陆账户即可读写(非root)
开机启动挂载共享目录
sudo vi /etc/fstab尾部添加
//192.168.2.142/md0 /home/tom/md0 cifs username="tom",passwo
rd="123456",iocharset=utf8,rw,dir_mode=0777,file_mode=0777,uid=1000 0 0至此对于单盘的添加就完成了,A机器的/home/tom/md0就是B机器的共享目录md0
也就是A机器添加Plot时,最终目录选择/home/tom/md0,生成好后直接就复制到了B机器的共享目录md0,也就是到了B机器的存储第一个硬盘里